
Understanding Search Performance Through Meaningful Written Content
Most websites do not lose rankings because of one dramatic mistake. It usually happens slowly….

Most websites do not lose rankings because of one dramatic mistake. It usually happens slowly. Traffic dips a little. Positions shift slightly. Then competitors begin appearing above you. When people start asking about How content impacts Google rankings, they are often trying to understand why visibility changes over time. The answer is rarely one single…

Life moves faster. Homes are empty more often during the day. Deliveries arrive when no one is around. Because of this shift, many homeowners spend time on checking a service trying to understand how protection can fit naturally into everyday life. This is where pace protections security systems often start to feel relevant, not as…

Working with document formats needs care, precision patience. Many people face output trouble when handling pdf to tiff tasks without checking basic settings. File clarity, size, balance page order matter during every step. Small mistakes lead to unreadable images, slow sharing, and storage waste. Understanding simple rules helps maintain quality, reduce rework save time. The…
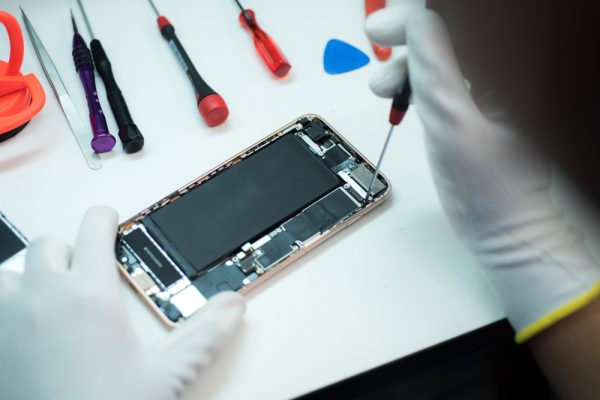
Modern devices support personal work study plus daily links. Skilled teams who understand mobile phone repairs focus on careful steps for every fault so owners feel calm and supported. Clear talk builds trust while steady care keeps every device useful for longer service life. Each repair plan is shaped with patience so the result feels…

Your phone slips from your hand. Glass meets concrete. That familiar crack spreads across the screen. It happens to everyone eventually. You need it fixed fast because your whole life runs through that device. Work emails pile up. Messages go unanswered. Even simple tasks become impossible without your phone working properly. Finding reliable phone repairs…

Real estate is moving toward a smarter phase where precision and timing shape success. Businesses now seek advanced systems that offer real insights and measurable value. Artificial intelligence brings data-driven clarity, helping experts identify patterns that were once hidden. This change is helping professionals connect faster with genuine buyers through focused campaigns and instant updates….

Efficient network upkeep ensures every system performs consistently well. When maintenance becomes proactive, downtime reduces, and stability strengthens. This steady performance also keeps devices communicating seamlessly through each process. With time, that consistent optimization directly enhances overall reliability for any website or connected platform. Predictive Checks Prevent Disruptions Monitoring tools detect irregular patterns before they…

Crafting detailed character origins often feels complex without clear guidance. Many writers explore new methods to overcome creative obstacles and inspire fresh ideas. One playful approach is using a Random Birthday Generator to quickly assign dates for character building. The technique works beautifully when combined with curiosity and thoughtful storytelling choices. Fresh Sparks For Creative…

Strong search growth begins with a clear plan and the right team. When you pick a provider, be sure to change the way you build links so each one feels real, fits the topic, and helps the main pages. strategic link building is not the same for everyone. A good partner will help you turn…

Today, organizations have to deal with more security risks and more complicated IT. Teams can improve security, build strong infrastructure, and speed up deployment with the help of devops consulting services. The right expert can help your team improve their methods, make plans, and get things done faster. Pay attention to skills, knowledge, and communication…